Computer Security Dieter Gollmann 3rd Edition
Schneier, Applied Cryptography, second edition, protocols, algorithms and source code in C, John Wiley & Sons Ltd, 1996. Pfleeger and S. Pfleeger, Security in computing, 3rd edition, Prentice-Hall, 2003. Dieter Gollmann, Computer Security, John Wiley & Sons Ltd, 2001. Kurose and K.W. Ross, Computer.
. Aland Islands. Albania.
Andorra. Armenia. Austria. Azerbaijan. Belarus. Belgium. Bosnia and Herzegovina.
Bulgaria. Croatia. Cyprus. Czech Republic. Denmark.
Estonia. Finland. France. Georgia.
Germany. Gibraltar. Greece. Greenland. Holy See (Vatican City State). Hungary.
Iceland. Ireland.
Italy. Latvia. Liechtenstein.
Lithuania. Luxembourg. Macedonia. Malta.
Moldova. Monaco. Montenegro. Netherlands. Norway. Poland.
Portugal. Romania. Russia.
Serbia. Slovakia. Slovenia. Spain.

Sweden. Switzerland.
Turkey. Ukraine.
United Kingdom. American Samoa. Australia. Bangladesh.
Bhutan. British Indian Ocean Territory. Brunei. Cambodia. China.
Christmas Island. Cocos (Keeling) Islands. Cook Islands.
Fiji. Guam. Hong Kong. India. Indonesia.
Japan. Kazakhstan. Korea (the Republic of). Kyrgyzstan. Laos.
Macao. Malaysia. Maldives. Mongolia. Myanmar.
Nepal. New Zealand. Pakistan. Papua New Guinea. Philippines.
Samoa. Singapore.
Solomon Islands. Sri Lanka. Taiwan. Tajikistan.
Computer Security 3rd Edition Dieter Gollmann Ebook
Thailand. Timor-Leste. Tonga.
Turkmenistan. Uzbekistan. Vanuatu.
Vietnam. Description Completely updated and up-to-the-minute textbook for courses on computer science. The third edition has been completely revised to include new advances in software and technology over the last few years. Provides sections on Windows NT, CORBA and Java which are not examined in comparable titles. No active previous experience of security issues is necessary making this accessible to Software Developers and Managers whose responsibilities span any technical aspects of IT security.
Written for self-study and course use, this book will suit a variety of introductory and more advanced security programs for students of computer science, engineering and related disciplines. Technical and project managers will also find that the broad coverage offers a great starting point for discovering underlying issues and provides a means of orientation in a world populated by a bewildering array of competing security systems. Completely updated and up-to-the-minute textbook for courses on computer science. Provides sections on Windows NT, CORBA and Java which are not examined in comparable titles. A top-down approach. No active previous experience of security issues is necessary making this accessible to Software Developers and Managers whose responsibilities span any technical aspects of IT security. New chapters on web applications security (cross-site scripting, JavaScript hacking, etc.) and more information on SQL injection.
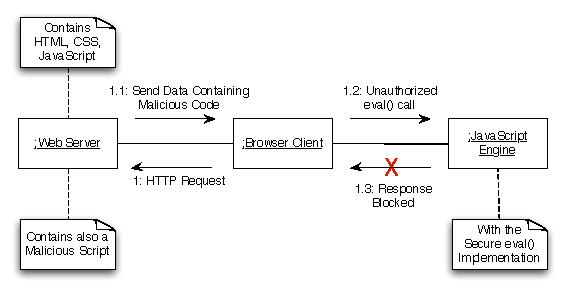
A completely up-to-date resource on computer security Assuming no previous experience in the field of computer security, this must-have book walks you through the many essential aspects of this vast topic, from the newest advances in software and technology to the most recent information on Web applications security. This new edition includes sections on Windows NT, CORBA, and Java and discusses cross-site scripting and JavaScript hacking as well as SQL injection.
Serving as a helpful introduction, this self-study guide is a wonderful starting point for examining the variety of competing security systems and what makes them different from one another.





